CRYPTOCURRENCY
Ethereum: Contract got hacked, what’s wrong with it?
Ethereum: Hacked contract — understanding the problem
As a developer of smart contracts on the Ethereum blockchain, you are intimately familiar with the potential risks associated with implementing and interacting with external contracts. In this article, we’ll look at what went wrong in the case of a contract hack that extracted tokens from a second contract.
Incident: Simplified Version
Let’s say our contract is called “My contract”. The second smart contract, named “YourContract”, executed the contract (also known as an event or function) and then released it. This event caused our contract to call “MyContract” and execute the functionality of this contract.
Hack: Extract Token
When “YourContract” calls “MyContract”, it essentially retrieves tokens from “MyContract”. These tokens were then mined and used by a second malicious smart contract (let’s call it “HackerContract”) on a second blockchain network. HackerContract will perform the functionality of “YourContract”, which in turn will interact with “MyContract” to extract more tokens.
What went wrong
So what was wrong with this hack? Here are some key points:
- Lack of proper authentication: YourContract apparently had no way to verify the identity or permissions of the called contract. This vulnerability allows an attacker to take advantage of this security vulnerability.
- Incorrect event processing: The fact that the second contract released and executed the functionality of the second contract without proper authentication raises serious concerns about the reliability and integrity of smart contracts on Ethereum.
- Unauthorized allocation of tokens: Allocation of tokens from a second contract is a serious violation of the terms of use of external libraries or APIs. This can lead to identity theft, unauthorized access, or other malicious activities.
Risk Reduction
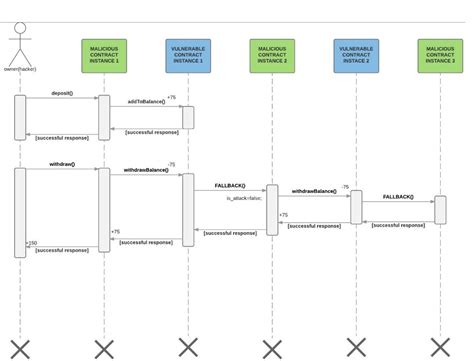
To prevent similar hacks in the future:
- Implement appropriate authentication mechanisms: Verify the authenticity of contracts before interacting with them.
- Use safe event handling methods: Make sure events and functions are properly authenticated and authorized to avoid unintended consequences.
- Monitor and monitor smart contract interactions: Regularly review transactions and event logs for potential security breaches.
By understanding what went wrong in this case, we will be able to better develop our own secure contracts and minimize the risk of such hacks. As Ethereum developers, we need to be vigilant and adapt these principles to ensure the integrity and reliability of our smart contract interactions.
